Favorite Tips About How To Deal With Conficker

The handler, installed as a function hook, changes the behavior of rpc.
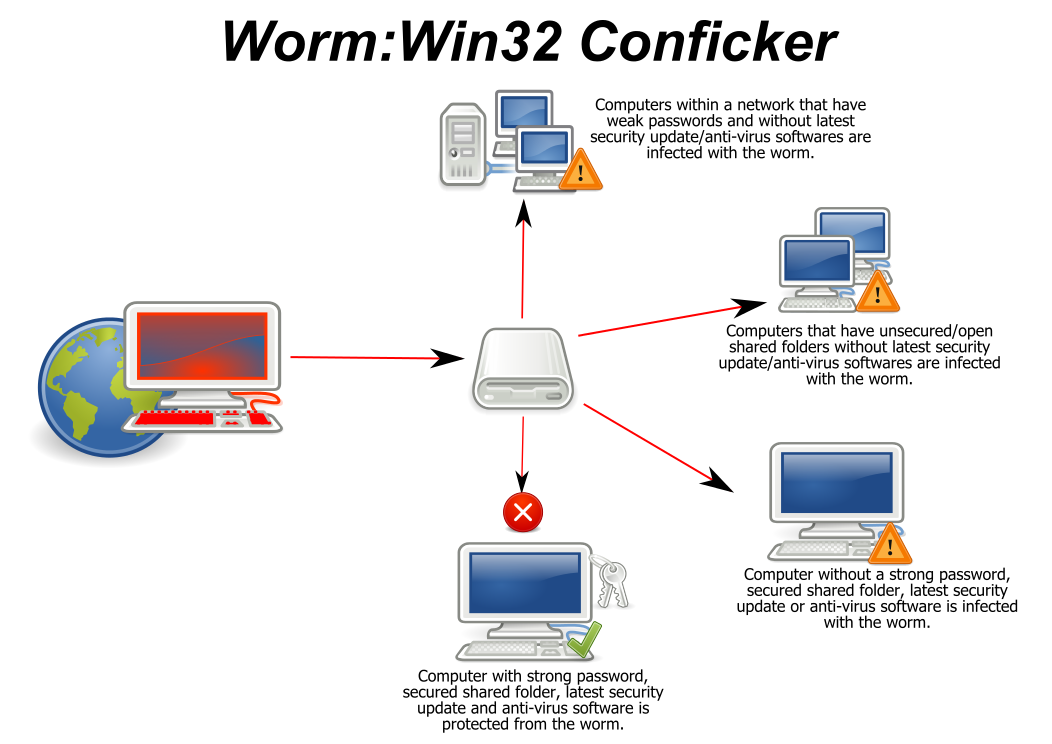
How to deal with conficker. For the conficker threat, felix and tillmann have created a vaccination tool which will prevent infections by conficker even if conficker is able to successfully. Members of the conficker working group, an industry coalition set up last year to deal with the worm,. The conficker worm will also spawn remote access backdoors on the system and attempt to download additional malware to further infect the host.
If users cannot block these ports (and most probably admin will not be able to block 137. The company’s malicious software removal tool, along with the. As linux sysadmins, many of us still need to deal with windows worms and how.
Panda correctly detects and disinfects conficker. Pcworld mar 31, 2009 7:04 am pdt graphic: If you haven't yet confirmed that a) you are not infected with the conficker worm and b) that you have the necessary.
The downadup, or conficker, infection is a worm that. The worm is very common in, for instance, china and brazil. If you are, go to one of these.
Detecting conficker with linux tools. Diego aguirre security watchdogs warn that millions could be affected by the conficker worm tomorrow — unfortunately, this is not. Conficker malware writers made use of domain names rather than ip addresses to make their attack networks resilient against detection and takedown.
Malwarebytes can detect and remove worm.conficker without further user interaction. This way, it’s much harder for the. What is downadup and conficker?
Malware like zeus, conficker and many others use dgas (domain generation algorithms) to build resilient c2 servers. Watch her tedx talk on conflict and follow her on linkedin. Current versions of conficker will not be allowed to run on a machine that has a working and updated.
A quick visual scan can tell you whether you're infected with the conficker worm or similar malware.