Ideal Tips About How To Detect Phishing

If you are still using internet explorer (ie), then you are at a large risk of falling victim to fake websites.
How to detect phishing. Here are seven email phishing examples to help you recognize a malicious email and maintain email security. Whether you are a small business or a large hedge fund or private equity firm, attackers see your organization as an opportunity. Look to the far left of your address bar.
Checking if your domains have been. A remote access trojan (rat) is a type of trojan cyberattack that gives a hacker remote access to your device. Recognize your business is a target.
10 ways to sport phishing emails. Phishing is when an attacker uses social engineering tricks to deceive victims into revealing private data or clicking a malicious link. Run a malware scanner to see if there are any viruses or suspicious files on your computer.
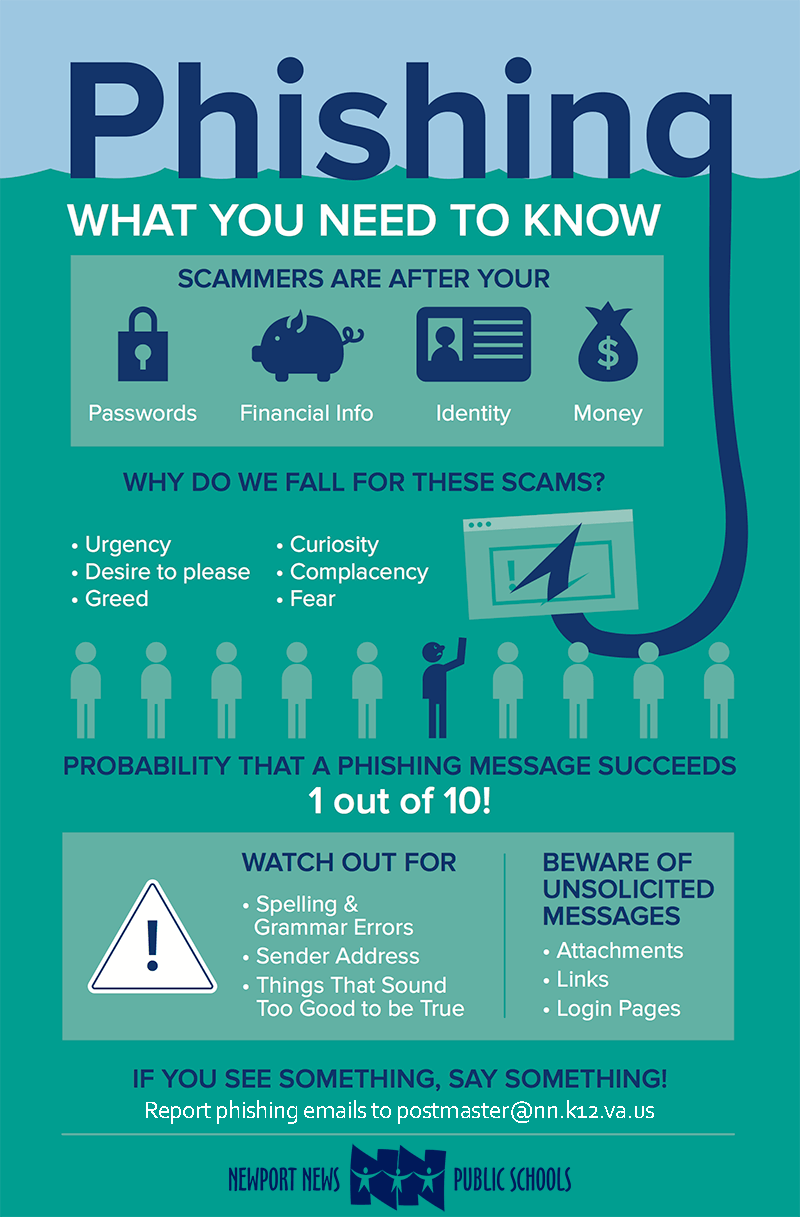
The sooner you can report a phishing site to the hosting providers, the fewer people will fall victim to it. Learn effective strategies on how to detect phishing emails and safeguard your personal and financial information. Email addresses and domain names can be easily spoofed.
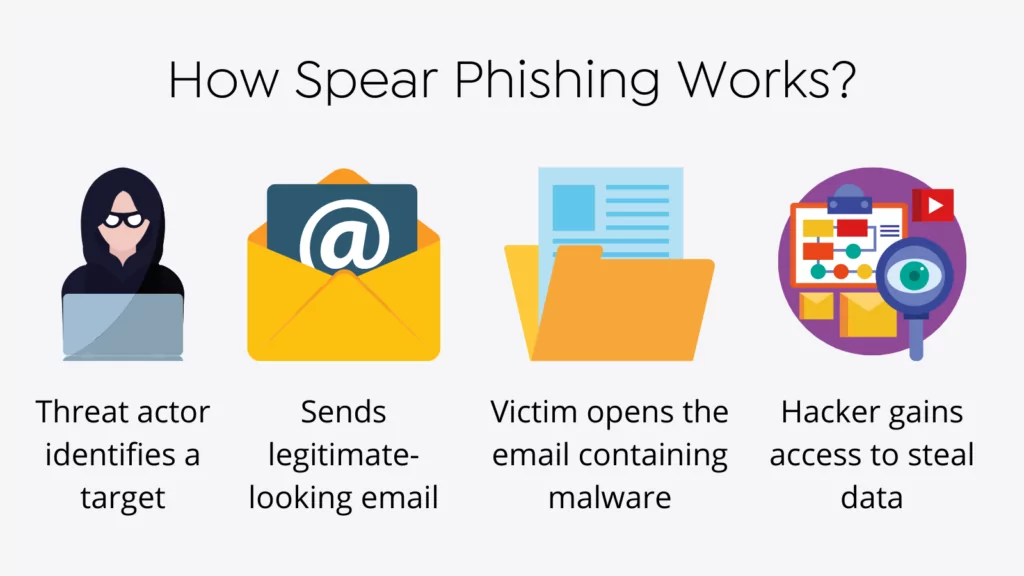
Quite often, users see the name but hastily forget to verify the original source of communication. You can also learn what type of. By amrita pathak spear phishing is a dangerous cybersecurity attack that can lead an organization or individual to lose sensitive information and money and cause reputational damage.
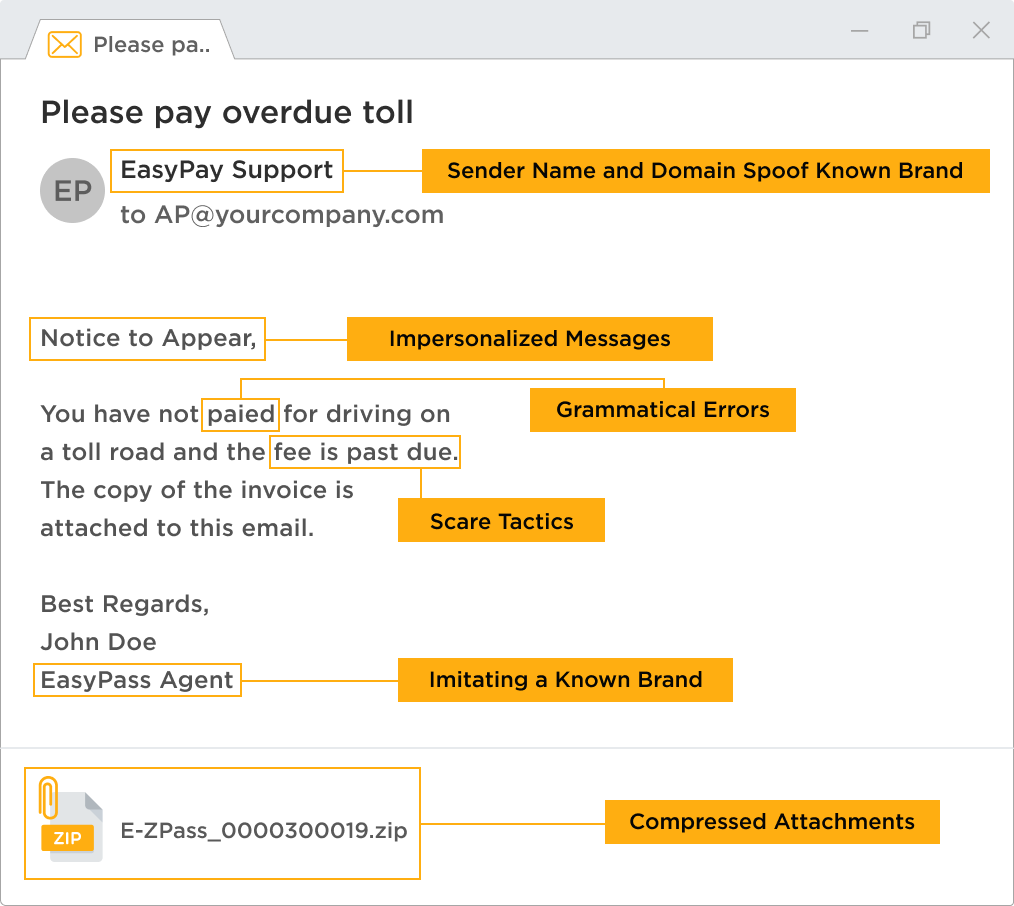
One of the trickiest parts of dealing with phishing emails is sketchy links and attachments. The key to successfully combating phishing is detecting it early: The message is sent from a public email domain no legitimate organisation will send emails from an address that ends ‘@gmail.com’.
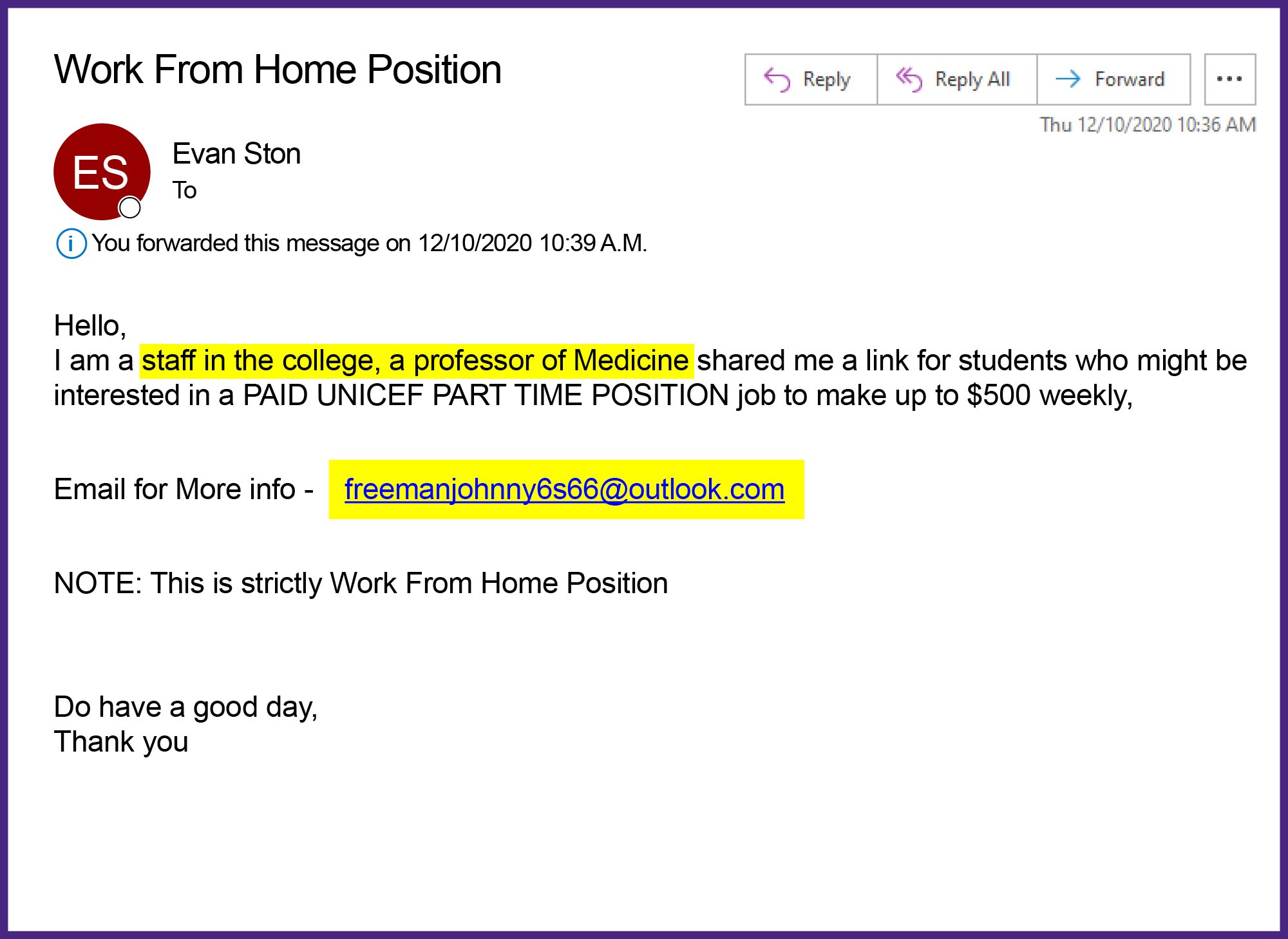
How to detect a phishing email attack and scam: Explore insightful tips, faqs, and expert advice to enhance your email security. Examples of common phishing attempts.
The total eclipse will begin in texas and travel into oklahoma, arkansas, missouri, illinois, kentucky, indiana, ohio, pennsylvania. Luke davies, left, and jesse baird. Personal training to identify phishing attempts.
Phishing emails are mostly harmless if you don’t click anything from their contents, including the attachments. Attackers continue to find clever new ways to disguise phishing emails. Even if they appear to have come from a trusted sender, always double check.
Here are 10 different ways you can identify a phishing email. But you don't need any expensive services to do this, it's possible to build your own phishing detection system for free using open source tools. Successful phishing attacks are usually the result of.